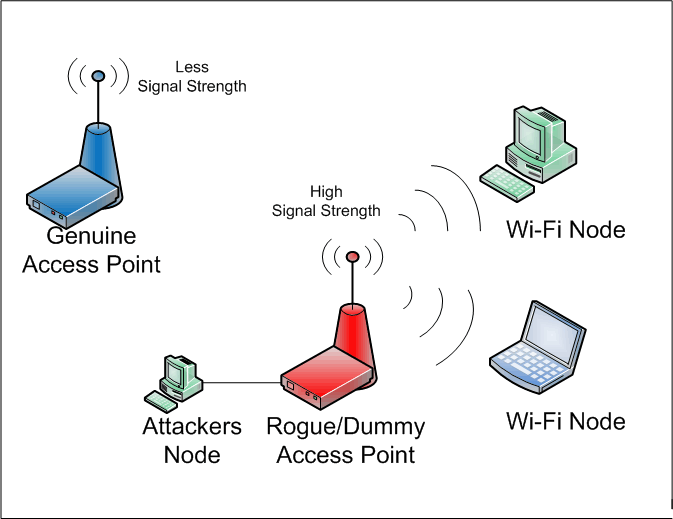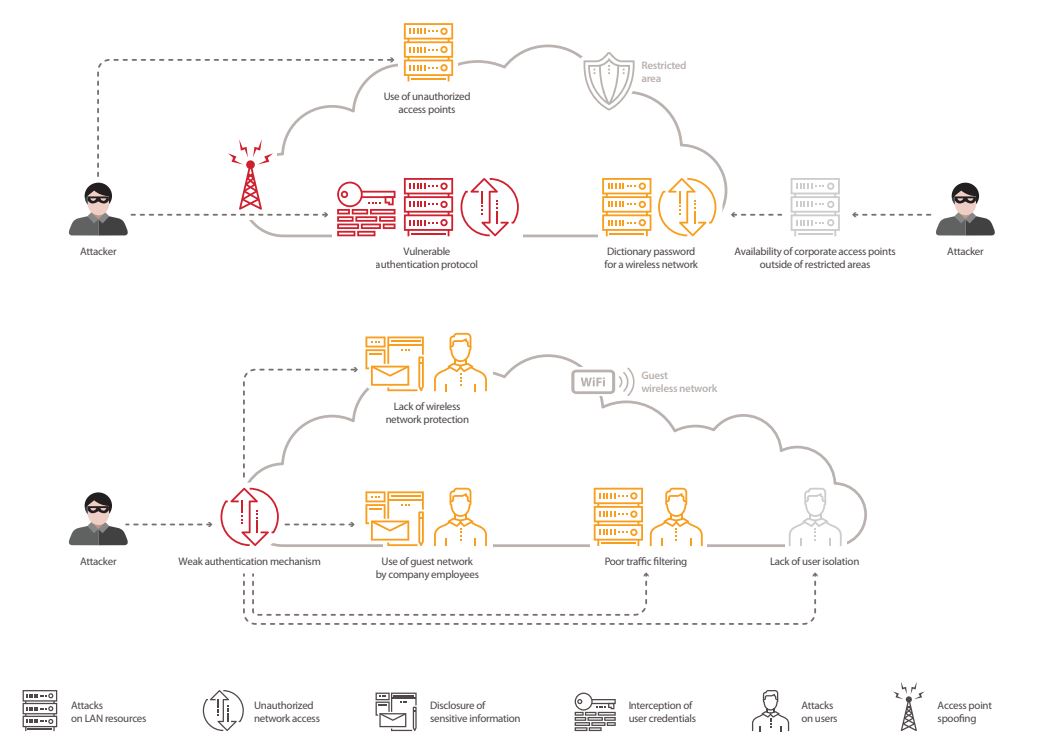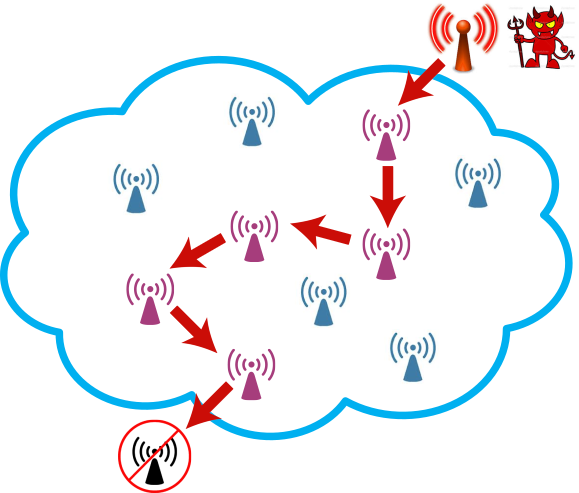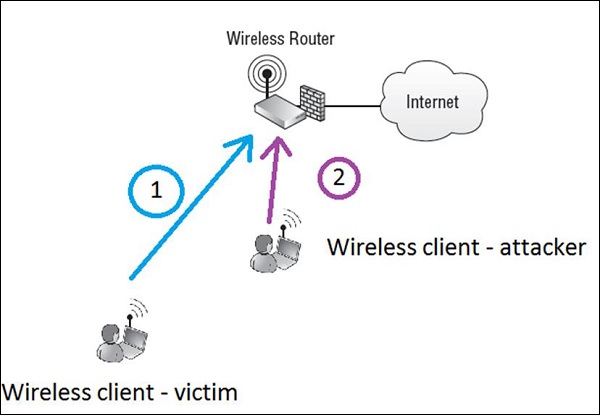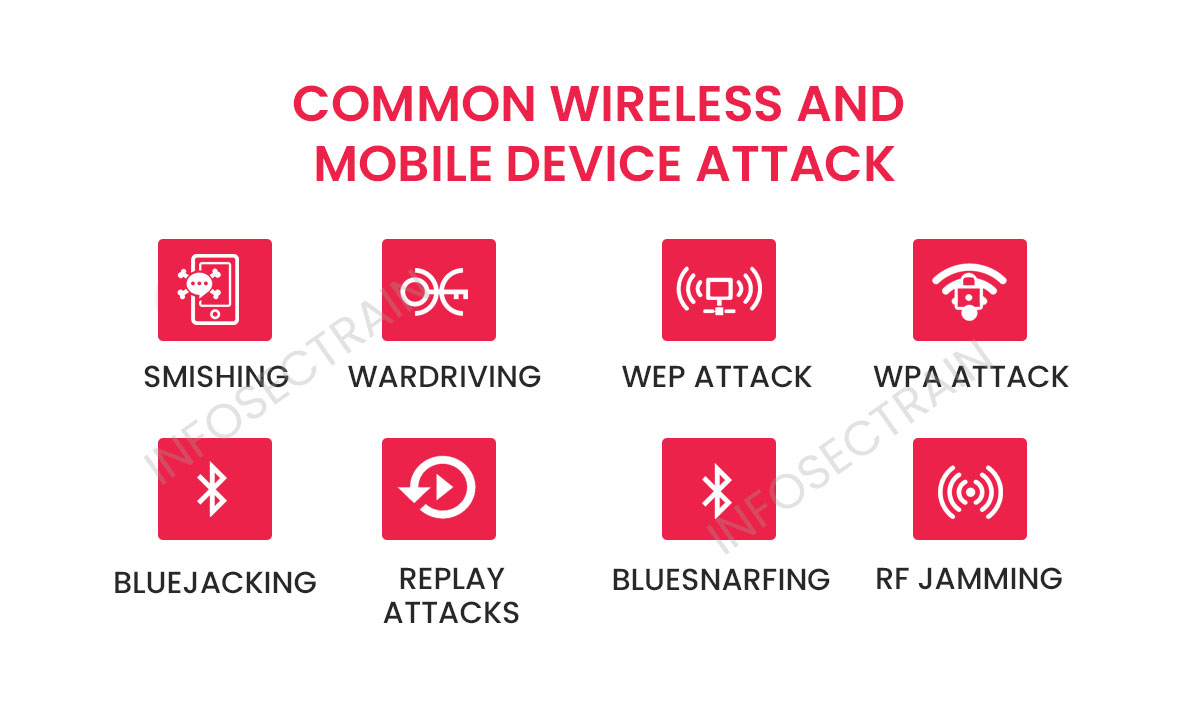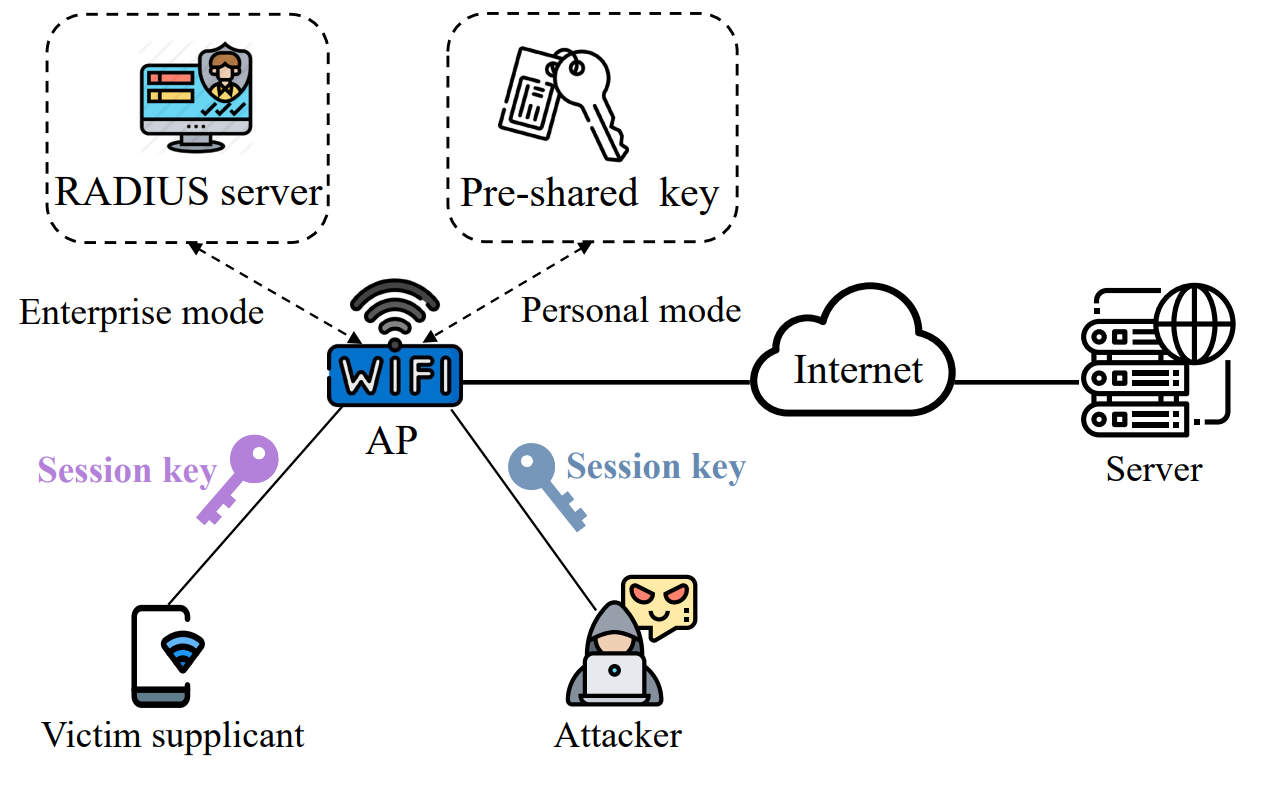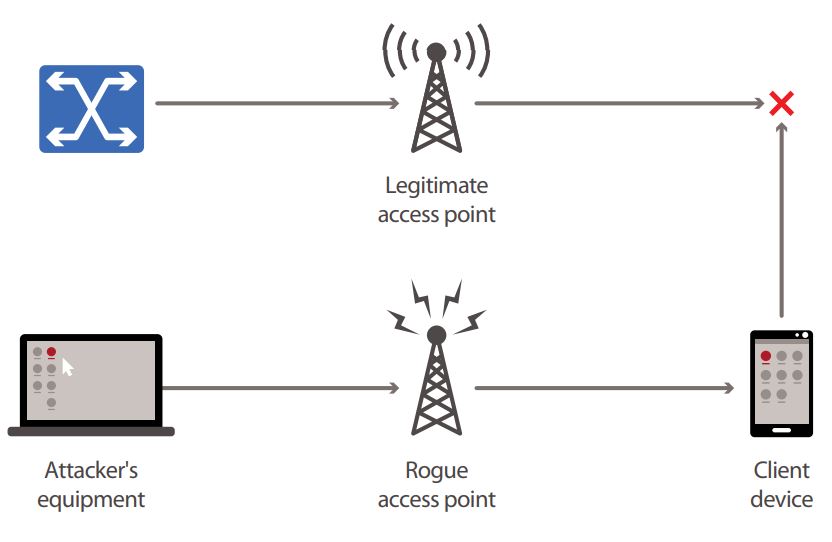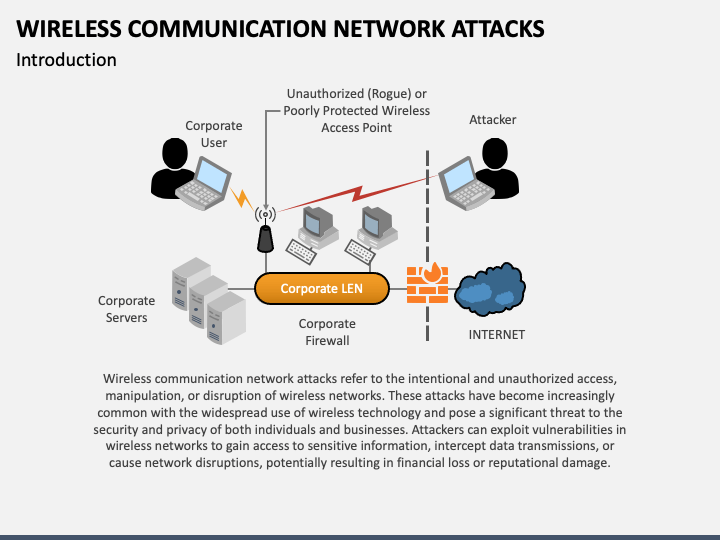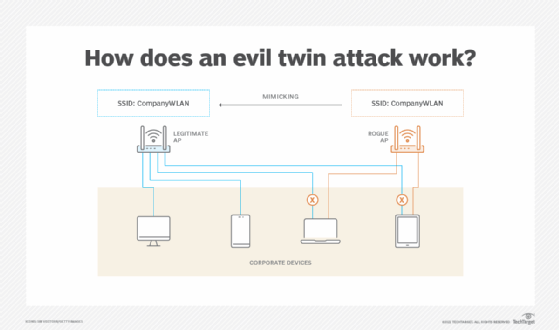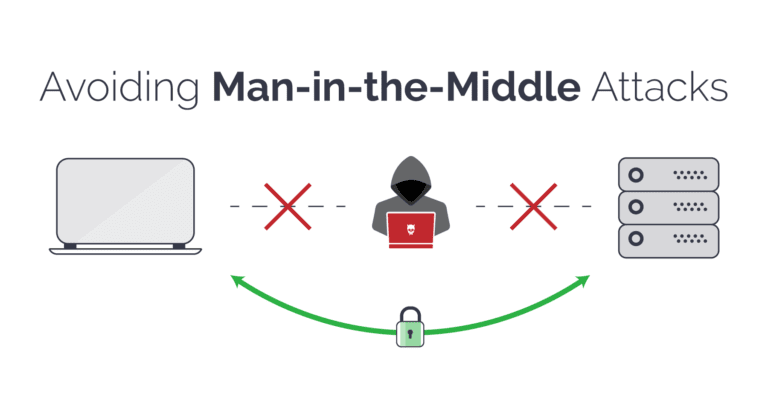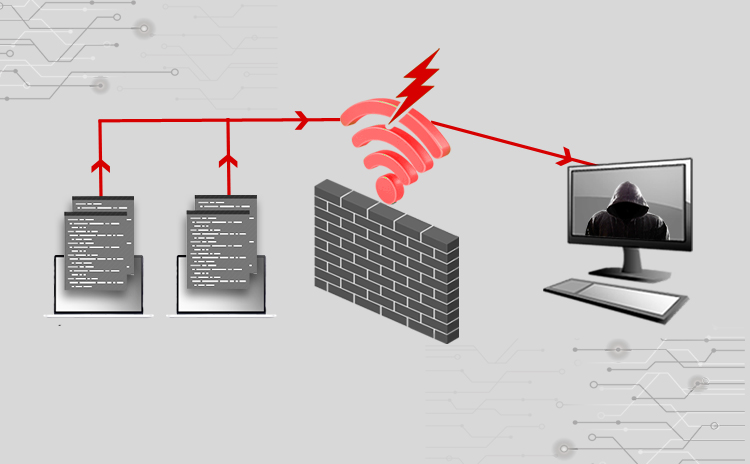
Cyber Attacks Explained - Wireless Attacks - Cyber Security Blogs - Valency Networks - Best VAPT Penetration Testing Cyber Security Company - Pune Mumbai Hyderabad Delhi Bangalore Ahmedabad Kolkata India Dubai Bahrain
![PDF] Analysis of attacks in IEEE 802.11 networks at different levels of OSI model | Semantic Scholar PDF] Analysis of attacks in IEEE 802.11 networks at different levels of OSI model | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/2bb39b43dd49e8c486c4a052fcc5d1a9349a50e7/2-Figure1-1.png)
PDF] Analysis of attacks in IEEE 802.11 networks at different levels of OSI model | Semantic Scholar